There are several reasons for using full disk encryption; sometimes it is a requirement of the company you work for, or maybe you have sensitive information that needs to be secured in the event of your computer being lost or stolen. While traditionally you may think of using BitLocker just for laptops because of their portability which brings an increased risk of loss or theft, this could be done on a desktop with the appropriate hardware required as well.
I will preface these directions with some cautions and warnings. The process although not rocket science, is a series of steps that must be followed quite closely with no variations. I myself have had some unsuccessful attempts at setting up the encryption, which caused an OS failure, and the need to reformat and reinstall the OS again. That being said... "BACK UP EVERYTHING IMPORTANT BEFORE SETTING UP ENCRYPTION!" Ideally, you would do this initially upon getting a new laptop with Windows 7, or after doing a fresh install. That way if you run into any major issues, you can re-image the machine to its default configuration and start over again. I do believe that encryption overall makes the hard drive a tad bit more volatile, so regardless of the success of encrypting your disk, I recommend backing up important files from time to time after encryption is complete.
There are a few prerequisites to using BitLocker and full disk encryption. 1st, you need to have Administrative rights on the machine. The 2nd I already spoke of and that is needing Windows 7 Ultimate. The 3rd is a device that is imbedded in the laptop or machine called a TPM or "Trusted Platform Module". The TPM is responsible for generating and storing a keyset used for the drive encryption and for integrity checks of the system boot files. This results in securing the system volume with encryption and integrity checking the system boot files to ensure that nothing has been tampered with and the system drive is located in the original computer. Only then is decryption preformed. While there are software only solution for full drive encryption, they are more susceptible to hackers than BitLocker used with a TPM. Microsoft has published a wealth of detail on the underlying workings of BitLocker and the TPM, so I will not repeat it here. If you are interested, check out either of the following sites:
BitLocker Drive Encryption Team Blog
TechNet: BitLocker Drive Encryption
Alright now to the meat and potatoes of this project. Remember, try to follow each step as closely as possible without deviation for the nest results.
Step # 1: Backup all important files. Let me say again... Back up all important files. Just in case you have any issue with setting up BitLocker, you will not have lost all of your important data.
Step # 2: Update the BIOS for your machine to the most up to date version. Each motherboard or machine is going to have their own website for instructions and downloading and updating the BIOS. For example Dell has a site for its updates, ASUS has a site for their motherboard updates, etc. Oh, and if you are reading this and not sure what the BIOS is... I recommend to halt this procedure and not continue. Just my advice.
Step # 3: Log into Windows after the BIOS is updated and go to the following: Start -> Control Panel -> BitLocker Encryption. Find your Hard Drive and select "Turn BitLocker On". It should probably not work giving you the message below stating a TPM could not be found. If for some reason the BitLocker process begins because your TPM was already configured, should cancel the process and do the 2nd part of Step # 4: Configuring the boot sequence from the BIOS.
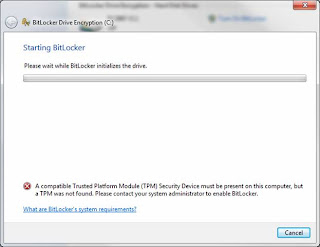
Step # 4: Enter the BIOS on boot and Enable the TPM and configure the boot sequence. 1st, enter the BIOS and find the TPM settings. They are probably under a 'Security' heading or something similar. All BIOS menus are different, so I don’t have the specific directions for each one, but navigate around until you find it. Once you do, select the option to enable it. 2nd, reconfigure the boot sequence. Make sure that any option for USB or Flash drives boot AFTER the Hard Drive. This sort of undocumented step caused me a lot of failed encryptions in later steps. The reason is that upon doing the BitLocker System Check, the system reboots and checks to make sure the generated keys placed on your USB Flash Drive actually work properly, prior to actually doing the encryption. Well if the USB is ordered to boot prior to the hard drive, the machine thinks you are using the USB as a boot device and forfeits the BitLocker check. You need to have the hard drive boot prior to the USB drive. No worries, though, if you ever need to boot from a DVD or flash, just go back in and switch the order to do whatever processing you need and then switch it back. Save your changes and exit the BIOS.
Step # 5: Set up BitLocker and the TPM. Log all the way back into Windows (do not shut down in-between) and go back to the BitLocker Encryption option in the Control Panel. Press "Turn On BitLocker" again. This time the BitLocker process will recognize a TPM enabled and being the process. You should see screens such as the following below:
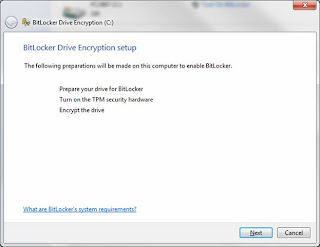
Press 'Next' to begin BitLocker preparations:
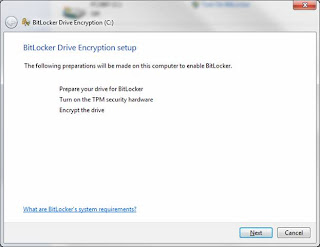
Press 'Next' to begin the allocation of space for BitLocker:
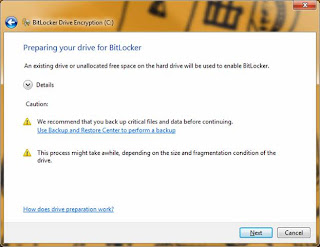
Press 'Restart Now' and allow the machine to reboot as displayed below:
Upon logging back into Windows, BitLocker will continue the process automatically, so do not attempt to open anything else. You will see the screen below, and to continue the process press 'Next':
Upon completing the steps above, you will be prompted to reboot the computer so that the TPM can be configures. Press 'Restart' as directed. Upon rebooting, you will see a basic MS-DOS old school looking screen informing you that the TPM has been modified and do you want to allow the modification. Allow the modification and follow the directions to press the appropriate button. In my case I selected the 'Modify' (not the 'Ignore') so that the TPM configuration could be modified. Upon completion, the machine will reboot. Log all the way back into Windows. The BitLocker process will proceed automatically again. You should see a screen like below:
One the TPM hardware has been configured you will see a screen like below; press 'Next' to continue the process:
At this point you will be prompted to save off the recovery keys. These are the keys that are stored in the TPM, and are only needed in the event of system tampering or breech. I recommend doing all (3) options, and storing the keys to a USB drive, printing them off, and saving them off to a location OTHER THAN the system drive (secure network share, etc.). Obviously I should not need to explains too much here that the keys regardless of type (paper, USB, file) need to be locked away. Don’t leave the USB on the desk next to the laptop, or the paper with the keys folded under the machine. That is like leaving the keys to the car in the door lock. Continuing on...press each option in the screen below to save off the keys:
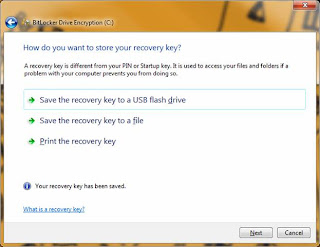
Step # 6: Run the BitLocker Check (USB with keys saved from Step # 5 required for this step). After saving the keys from above, press 'Next. You will see the screen below asking if you want to run the BitLocker check. While not required, I recommend doing it. You don't want to encrypt the drive until you have tested that the generated keys actually work. Check the box to run the BitLocker check and make sure that the USB drive IS INSERTED in the machine. Press 'Next' and the following reminder and reboot screens will be displayed:
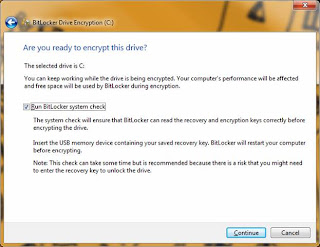
Step # 7: Full drive encryption. Upon a successful reboot and USB keys check, the BitLocker process will automatically being the encryption process of the system volume. This will take several hours depending on the size of the drive, but you can continue to work in the background if needed. However, do not reboot or shut down during the encryption process. You can lock your machine if needed. The encryption dialog (shown below) will display the progress.
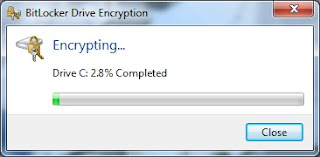
Step # 8: Configure the machine policy to require a pre boot PIN + TPM (Optional). Once the encryption is complete, you are technically done. The drive is encrypted and secure. You will notice upon reboot you are never prompted for the keys or a password. That's normal. The TPM has the keys, and if there was any breech or integrity failure, you would be prompted for the keys. Otherwise the authentication occurs in the background and is seamless.
However, to strengthen your security you may want to configure a pre boot PIN that works separately but in conjunction with the TPM. To accomplish this, follow Step # 8 and Step # 9 and Step # 10.
We need to open the Group Policy editor for the machine. Goto Start -> and type in gpedit.msc and press 'Enter'. Then Goto: Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives and right click the option "Require additional authentication at startup" and select "Edit". The screen is displayed below:
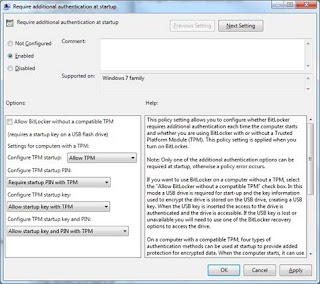
Select "Enabled" and then select "Require startup PIN with TPM" under the "Configure TPM startup PIN:" dropdown. Click "Apply, "OK" then close the dialog and Group Policy editor. This now allows us to configure the pre boot PIN from the command prompt.
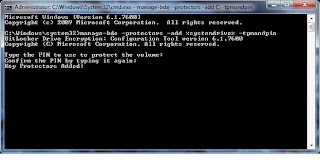
Step # 9: Goto Start and type in cmd but do NOT press enter. Once the cmd application displays in the start menu, right click it and state "Run as Administrator". Click "Yes" on any security dialogs that may appear. To configure the pin we need to use the manage-bde.exe tool. To configure the PIN, enter the following and then press 'Enter':
manage-bde -protectors -add %systemdrive% -tpmandpin
You will be prompted to enter a PIN. (Note: I did notice if you still have the USB with the keys inserted into the machine, this process does not work - the command prompt never asks you to enter the PIN; make sure to remove it before doing this process). The PIN by default can only be numeric. There is an option in the group policy editor from Step # 7, to allow complex PINs for this process, but wars not all systems support it. Since you may not find that out until reboot, and not be able to log back in, I suggest just using a numeric PIN. You will be prompted to enter it twice, and upon success, see a screen like the one below:
Step # 10: Reboot and test the PIN. Upon rebooting, after the quick flash of your system manufacture screen, you should receive an old MS-DOS style screen prompting you for your PIN. It tells you the function keys can be used to represent numbers, but I always just use the keypad and it works fine. If needed, the option is there. Upon entering the correct PIN the machine will continue booting into Windows. One note on the pre-boot PIN: I have found that if you have your USB containing the keys inserted upon boot, it assumes you are validated and skips the prompting of the PIN. Since your USB drive should be locked away, you will be prompted for the PIN, but again, another nice option if needed.
And that is it! Hopefully your encryption process went well and you are complete at this point. I have done this process on 7 different machines with success, so I know it works when followed as directed. Your drive will now be secure with BitLocker.
You are a stud when it comes to this. Best narrative tutorial I ahve seen yet. Question for you and a challenge! How would one set the pin for a dual boot Vista and W7 on seperate paritions and a seperate data drive. All are BitLockered. Is it one pin? Will check back for answer. Thanks in advance.
ReplyDeleteGreat tutorial. How would one implement this on a dual boot Vista and W7 with bit locker on both currently using TPM only. The OS' are on seperate partitions. Also, have a seperate data drive also bit lockered and "managed" by both OS'. Thanks!
ReplyDeleteGreat tutorial, best one I’ve seen as far as user friendliness for the less technically inclined. Question for you regarding adding a PIN to an existing setup using only TPM. The current set up is as follows: Disk 1 has Vista 32 and Windows 7 64 on a dual boot. The OS’s are on separate partitions. Disk 2 is simply a data drive. Bit Locker has been set up successfully on both Vista and Windows 7 and the machine dual boots perfectly. Disk 2 is Bitlocker “managed” perfectly. How does one go about adding a PIN to TPM? Do it through W7? Vista? Both? Thanks so much in advance.
ReplyDeleteThank you for reading, and I am glad that the tutorial is helpful. I want to address the several questions about dual boot machines, with each drive individually encrypted with BitLocker.
ReplyDeleteIt is important to explain that regardless of the number of individual physical or virtual drives encrypted by BitLocker, the TPM holds the keys 1..n for each drive (as I understand). Setting up a pre-boot PIN prevents access to the TPM releasing the sealed keys to the OS until the correct PIN is entered. Therefore, I believe it does not matter which OS you use to initiate setting up the PIN (using manage-bde.exe) as it will apply to the TPM as a whole. I would recommend setting up the PIN in your Windows 7 OS, as that is the one I have provided for the directions.
You will notice that once the pre-boot PIN is set up and you reboot, that the prompt screen for the PIN comes very early, in fact immediately after your manufacture or motherboard splash screen. This PIN is 'Pre' boot, so therefore the TPM will not release the keys to even get you to the Windows screen to select which OS to boot from until the PIN has been entered. I believe once you set up the PIN via Windows 7 and then tried to set up another PIN in Vista thinking there would be (2) would cause the manage-bde.exe commands to come back and tell you a PIN was already set up for the TPM.
Now I must add that I do not have a dual boot machine to test all of this on, but this is from information I understand and have gathered. As I always claimed in the article, BACK-UP, BACK-UP, BACK-UP your drives prior to trying any potential 'unknowns'. However from the technical documentation I have seen the TPM can be protected with additional authentication via a pre-boot PIN, but there will only be 1 PIN for the single TPM that exists within the machine.
I have found some great articles to help explain the TPM and its workings that you may want to read over to be more familiar with the TPM + PIN setup I have outlined. Take a look below and report back if any of your findings in setting up the pre boot PIN on a dual boot system ('after' backing all of your drives :)) are different than the information provided.
Keys to the Kingdom: (nice diagram and explination of the keys and TPM)
http://blogs.technet.com/bitlocker/archive/2006/08/01/bitlockerkeys.aspx
BitLocker Drive Encryption:
http://www.anvir.com/bitlocker-drive-encryption.htm
BitLocker Drive Encryption in Windows 7: Frequently Asked Questions:
http://technet.microsoft.com/en-us/library/ee449438(WS.10).aspx#BKMK_YouBrute
What is a BitLocker Drive Encryption startup key or PIN?
http://windows.microsoft.com/en-US/windows-vista/What-is-a-BitLocker-Drive-Encryption-startup-key-or-PIN
Thanks again for reading!
Allen, wonderful! Thanks for the clarification. Just a question after reading your latest work and also looking at Technet. IS the difference between your method and Technet’s (copied below) which has
ReplyDelete“-delete“and then an “–add”command, due to you going through the group policy GUI instead? So the GUI, if I am understanding correctly, takes care of the first command “–delete”? Just want to double check (to avoid messing things up). Thanks again. M.
http://technet.microsoft.com/en-us/library/ee449438(WS.10).aspx#BKMK_Key
Is it possible to add an additional method of authentication without decrypting the drive if I only have the TPM authentication method enabled?
You can use the Manage-bde.exe command-line tool to replace your TPM-only authentication mode with a multifactor authentication mode. For example, if BitLocker is enabled with TPM authentication only and you want to add PIN authentication, use the following commands from an elevated command prompt, replacing <4-20 digit numeric PIN> with the numeric PIN you want to use:
manage-bde –protectors –delete %systemdrive% -type tpm
manage-bde –protectors –add %systemdrive% -tpmandpin <4-20 digit numeric PIN>
I want to do the enhanced PIN thing, so am looking at the Local Group Policy Editor Screen now. A snippet from Technet shows:
ReplyDelete1. If you are using PINs for authentication along with the TPM, you may want to enable the use of enhanced PINs to allow for increased complexity of PINs. Enhanced PINs support the use of characters, including uppercase and lowercase letters, symbols, numbers, and spaces. Not all computers support these characters before the operating system starts, so we recommend that users perform a system check during BitLocker setup to verify that their computer will support the BitLocker settings they have selected before encrypting the drive. Double-click the Allow enhanced PINs for startup policy setting, and click Enabled to provide the option of using enhanced PINs with BitLocker-protected operating system drives. If this policy setting is disabled or not configured, enhanced PINs cannot be used.
2. After you have made your choices, click Apply to apply the settings, and then close the dialog box.
3. Close the Local Group Policy Editor.
4. To force Group Policy to apply the changes immediately, you can click Start, type gpupdate.exe /force in the Search programs and files box, and then press ENTER. Wait for the process to finish.
By completing this procedure, you have configured Group Policy settings to control which unlock methods can be used with operating system drives in your organization
The Local Group Policy Editor Screen shows a line for “Allow enhanced PINs”. Do I do the “force” in step 4 above then go back and make the changes your outlined previously? OR is simply clicking OK and then going back and using the other screen as demonstrated by you? Thanks again M.
PS my PC manufacturer’s (Lenovo Thinkpad) splash screen comes up then I’m allowed to enter a password under normal non BitLocker circumstances. Can I assume it allows enhanced PINs?
This was tried on a dual boot using the Win7 GPE GUI exactly as you have in your picture. When rebooting, it does not ask for a PIN. Seems the TPM takes over and allows the system to boot just as if there were no PIN. Thinking the options boxes are mutually exclusive, I selected REQUIRE TPM + PIN and DISALLOWED all the other choices including TPM (only). Rebooted, still does not work. Yes, the PIN was set up correcly using the CMD prompt as it asked for it twice (ie repeated the PIN). What next? Did not try the Vista GUI tab where there IS some mutually exlusive choice. Baffled. Disable BL and renable for the Group Policy to take hold?
ReplyDeleteBecause it did not work I went back to the gpedit.msc GUI in W7 and just clicked the NOT CONFIGURED BOX. Also did the same for Vista.
ReplyDeleteIs it necessary to somehow delete the "manage-bde -protectors -add %systemdrive% -tpmandpin"
to avoid corruption prospectively? If so how?
Additional follow up. IMO the reason it does not work is in a dual boot an S parition is actually created so the pre-boot IMO is moved to the S. So messing with the C volume does no good as the files are in the S volume. How to work it so that a PIN is added for both OS'?
ReplyDeleteAt this point several good questions have been asked in reference to setting up BitLocker on a dual boot machine and specifically in regards to the pre-boot PIN setup in this environment.
ReplyDeleteUnfortunately, I do not have a test environment or machine with this setup to test setting up the pre boot PIN under these conditions. I suggest you open a forum thread on the 'Windows 7 Security Forum' in regards to the pre boot PIN setup for BitLocker on a dual boot machine with 2 different operating systems. If you find the answer, please post back or link to the forum for future readers, or I can update the post.
Here is the link:
Windows 7 Security Forum:
http://social.technet.microsoft.com/Forums/en-US/w7itprosecurity/threads
Thank you,
does manage-bde -protectors -add %systemdrive% -tpmandpin
ReplyDeletemean manage-bde -protectors -add c: -tpmandpin
as far as what to actually type in?
Thanks!
%systemdrive% is an Environmental variable defined by windows and represents the drive where Windows is Installed. If Windows was installed to C: then that would be correct.
ReplyDeleteAllen thanks. The thing is on a dual boot what is the C drive seems to be dynamic in that it could be W7 or Vista or whtever OS you boot into. So given that I misunderstood your directions as far as %systemdrive% intended to represent C:, what do you think of using mean manage-bde -protectors -add c: -tpmandpin
ReplyDeleteAND manage-bde -protectors -add d: -tpmandpin with d representing the other OS as viewed through manage-bde. For some reason my other OS is lettered not D in Windows now after the first attempt to set it up. I figure the most accurate is what manage-bde says which is still D.
I can safely say after many attempts, this does not work for a dual boot. Even after treating the options in the W7 and Vista group policy GUIs as mutually exclusive choices ie REQUIRE TPM AND PIN and DISALLOW for others on both GUIs. Maybe the solutions is make command line changes and skip the GUI but seems risky. Any thoughts people?
ReplyDeleteThank you .. thank you & thank you. :-) Was searching high and low for this set of instructions and once I found this page .. it was all smooth sailing for me. WORKS GREAT on my Win7 Ultimate!!
ReplyDeleteHey guys, did all the steps, get the following error after running the command "manage-bde -protectors -add %systemdrive% -tpmandpin"
ReplyDeleteC:\Windows\system32>manage-bde -protectors -add %systemdrive% -tpmandpin
BitLocker Drive Encryption: Configuration Tool version 6.1.7600
Copyright (C) Microsoft Corporation. All rights reserved.
Type the PIN to use to protect the volume:
Confirm the PIN by typing it again:
Key Protectors Added:
ERROR: An error occurred (code 0x80310060):
Group Policy settings do not permit the use of a PIN at startup. Please choose a
different BitLocker startup option.
Any ideas?
We don't have group policies implemented here.
Ramon -
ReplyDeleteEven if your domain administrator does not actively push out any Group Policy updates, you still need to configure the local machine policy to enable setting the PIN. The machine will NOT allow adding the PIN by default, and you must follow the steps I laid out using the Group Policy Editor (gpoedit.msc) prior to running the manage-bde.exe tool. It allows the addition of the pre-boot PIN, and should process properly without error once you have done that step.
Hey - thanks for the post - most interesting and very clear.
ReplyDeleteCan this be done via domain group policy? (The PIN that is...) I am looking for a way to centrally manage the user’s pre boot PIN numbers.
Thanks
Oh by the way, for the commenter named 'Melissa', I ran accross this article on TechNet that you may find interesting:
ReplyDeleteCan I dual boot Windows 7 and Windows Vista with BitLocker-protected operating system drives?
http://technet.microsoft.com/en-us/library/ee449438(WS.10).aspx#BKMK_dualbootW7Vista
I was asked if the pre-boot PIN can be managed and pushed out via a Group Policy. I believe the answer is Yes, but I have almost no experience (actually none to be exact) in being a domain administrator that manages domain group policies. I recommend checking out the following link:
ReplyDeleteWindows Server Group Policy Home:
http://technet.microsoft.com/en-us/windowsserver/bb310732.aspx
Thank you for reading!
Great post, however if you get the error Group Policy settings do not permit the use of a PIN at startup. Please choose a different BitLocker startup option.
ReplyDeleteMake sure the machine is connected to the network when running the manage-bde command (this solved it for me at least).
Allen, nice and helpful writeup. On your “require authenication at startup” tab why do you uncheck the “allow Bitlocker without a compatible TPM”? this has no impact on the ability of the recovery key to function?
ReplyDeleteAlso what are your thoughts on using Bitlocker to encrypt the recovery partition (partition on most computers now to restore the OS)? I did it and in testing it it just asks for the recovery key. On thinkpads and I assume some other notebooks, one has to go to the recovery screen to get to the BIOS. Figured this would block access completely (in addition to BIOS password) but a little afraid I might be setting myself up for an expensive problem should my HDD or something fail.
USB Removeable HDD/ Bitlocker TPM and PIN/ Group Policy Error!!!!!
ReplyDeleteScenario
1) BL properly set up and functioning fine with TPM
2) OS drive is protected
3) Removeable USB drive set up to automatically unclock
4) Boost to TPM and PIN instead of just TPM to unlock BL
5) Plug in another USB drive and attempt to set up BL. Problem: Get message that Group Policy Settings are in conflict and BL cannot be set up. Went into GPEDIT.MSC (elevated command) and changed “control use of BL” on removeable drives to ENABLED. Used gpupdate.exe /force to force changed immediately. Am still getting message that Group Policy Settings are in conflict and BL cannot be set up.
Adding the PIN seems to have done something as the first removeable drive which was set to auto unlock on the PC is OK. Seems the USB drives have to be added before switching from TPM only to TPM and PIN.
Any work around????
" On your “require authentication at startup” tab why do you uncheck the “allow Bitlocker without a compatible TPM”? "
ReplyDeleteActually I do not deselect that option; it is the default. Checking it would override that option and essentially state that BitLocker 'could' be set up without a compatible TPM.
"Also what are your thoughts on using Bitlocker to encrypt the recovery partition"
I would have to dig through the documentation again, but I am pretty sure that when an entire OS drive partition is encrypted, the boot files etc, are placed on a separate partition that is not encrypted and this is done all by the BitLocker setup. If you tried encrypting the recovery drive, I am not sure if it would work the same or be successful. My walkthrough was really the 'Vanilla' process of encrypting a single drive. I am not sure if you would really need to encrypt the recovery drive regardless because there shouldn’t be anything on it sensitive to need encryption. It is just the files and default image to restore a machine. I recommend if you want to try doing it on a TEST machine and not your primary in case something goes wrong.
You have helped me a lot Allen. Thank you.
ReplyDeleteBut I do have my two cents worth. The PC is with Win7 is being used in a small busuness - three employees. The PC contains the full accounting system, employee and customer information. Backups are done to a USB stick, which has been very successful for ten years. The owner dislikes the idea of connecting to the internet. The concern is theft of the PC and loss of the usb stick.
So the drive and the USB stick have to be encrypted, and we want the additional protection gained by using a pin. After completing steps 8 and 9, I found that the backup on the USB stick can be used on any PC after the correct pin has been entered. This is great, he can take his work home. The point is Its key is not stored in the TPM.
As others have pointed out, there is a clash of group policy. After enabling "Require startup pin with TPM" . Everything worked great, except I was not able to set a pin for the USB stick. The error message received was "Group Policies settings do not permit the use of a PIN at startup ....". In GPEdit I had to set "Require Additional authentication at startup" to "not conifgured" just so that I could set a pin for the USB stick, then reset it afterward.
This make setting a pin for the USB stick a little beyond the ability of the average user. Its probably a wonderful feature, but I only spent a couple of hours trying different settings. Quite likely someone has found a better way of solving this issue. I would be very interested reading it.
Regards David
You are a God
ReplyDeleteExcellent!
ReplyDeleteI have a home built PC with an Asus MOBO. I purchased a TPM and it works fine. The numeric PIN works fine. How can I tell if an enhanced PIN would work? I see the option in the GPO to enable it. I have Bitlocker running on my OS. How can I at this point tell if I check the enhanced PIN if my computer will take it?
ReplyDeleteExcellent instructions except that in my case after enabling TPM+Pin in gpedit at the elevated command prompt it prompts me to type in the numeric Pin but it won't let me type anything in [just the cursor flashing]. I am now decrypting the drive and starting again. Any ideas?
ReplyDeleteI too have followed all of your instructions and gotten to the point where I was to enter the numerical PIN and could not enter anything???
ReplyDeleteHi Allen, I used this procedure years ago to encrypt some of our machines here at work. I'm having issues with one of the machines and would like to rebuild the OS, what is the Command to remove the TPM requirement at bootup? I tried disabling the TPM requirement in the group policy but am still getting the requirement for it at bootup. Any help to remove this would be appreciated
ReplyDeleteHi Allen,
ReplyDeleteI know this is a very old post but I've used your process for some time. If one needs to rebuild the machine that was encrypted this way how would you remove the TPM requirement (same question as the last person to post here apparently)
Allen have you done his dual booting W7 and 10?
ReplyDelete